Proof of Work: Definition, How It Works.

The Proof of Work protocol, or Proof of Work, is the best known and oldest consensus protocol, it consists of the parties of a network successfully performing a computationally costly job in order to access the network’s resources.
Introduction
It is a consensus algorithm based on complex mathematical operations that must be performed by a computer. Proof-of-Work requires a significant, but feasible, amount of computation. It serves to deter malicious attackers who want to launch a denial-of-service attack or a 51% attack.
Proof-of-Work, PoW, is a mechanism used for transaction confirmation and new block generation, these blocks are necessary to process and store new transactions in the blockchain. To perform these validations, miners compete to validate transactions.
In exchange for their computational work, miners receive a reward, such as bitcoin, when they validate a transaction. In order to validate these transactions, a complex mathematical puzzle must be solved by these miners next to the simple proof of the solution.
One of the reasons for using proof-of-work is to avoid double-spending attacks. It also seeks to make performing a 51% attack so costly that it is not feasible to launch one of these attacks. These 51% attack is the worst-case scenario, and refers to a situation where malicious actors could take control of a certain blockchain network.
Origin of Proof-of-Work
One of the biggest growing problems in the 90s, as the Internet became popular, was spam. We are talking about the massive sending of unwanted emails by the end-user. Sending thousands of emails is very easy and the cost is minimal for those who want to send them. A system called Proof of Work was devised for this purpose.
In 1992, Cynthia Dwork and Moni Naor, workers in IBM’s Research Department, devised the Proof-of-Work algorithm to combat spam. This mechanism requires the sender to do a small job that is added to the mail as a signature. This job costs just a few seconds, just enough to make spam costly in time and resources. And is that spam is based on sending hundreds or thousands of emails in the least amount of time possible.
Adam Back, in 1997, picked up this solution to combat spam and added it to his project to counter spam, called HashCash. The interesting thing about Back’s solution is that it uses virtually the same cryptography that Bitcoin technology uses today. Satoshi Nakamoto, in the Bitcoin whitepaper, mentions the solution developed by Back.
This means that the Proof-of-Work consensus algorithm is much older than its implementation in Bitcoin. Although it was initially developed to combat spam, it has become a security system for cryptocurrencies.
How does PoW work?
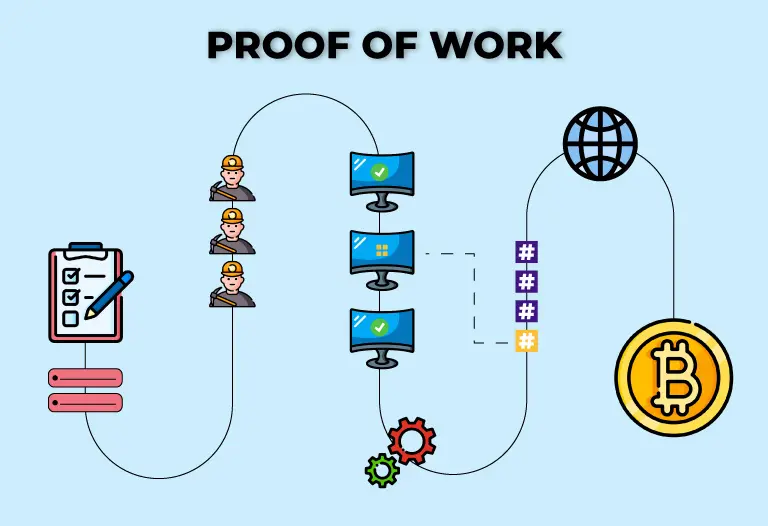
Protocol consists of four (4) major stages:
- The client or node establishes a connection with the network to solve the puzzle in order to receive an economic incentive.
- It proceeds to solve the puzzle, which involves high resource usage and computational costs.
- Once solved, the client shares with the network for verification. If the result is positive, access to network resources is provided, otherwise it is rejected. This is where double-spend protection checks come in, preventing a previously assigned task from being submitted more than once.
- The miner receives a reward (profit) for the computational work and the client’s transaction is then completed.
With this, PoW is enabled and modeled. The blockchain has given great utility to this method by providing high levels of security and low complexity, allowing millions of people to participate in this network.
Conclusion
The proof-of-work consensus mechanism has the strength of being highly secure and penalizing malicious attackers. In order to manipulate a transaction or the movements on a network, for example, we would currently need a brutal amount of hardware, which has a very high cost. In addition, we would need enormous amounts of electrical power.
It is important to understand the potential vulnerabilities of a blockchain network. this strength, in smaller cryptocurrencies, can be a problem, as has already happened with Vergeoin, which suffered a 51% attack some time ago.
The good thing about this mechanism is that it adapts perfectly to hardware changes and the entry and exit of miners from the network. It introduces certain mechanisms which adapt the difficulty of mining according to the computational power of the network and the number of network members. It is also positive that manipulation attempts have huge computational power, time and energy costs. This last parameter, energy, is the weak point of the proof-of-work consensus and used by cryptocurrency detractors to launch attacks. Although precisely this cost in electrical energy is what gives security to cryptocurrencies and Bitcoin.
What do you think about the proof-of-work? Is it a good thing for the security it offers or is it just a waste of energy and resources?
What do you think about the proof-of-work? Is it a good thing for the security it offers or is it just a waste of energy and resources?
Disclaimer: This is a contribution post made for Globalcoinresearch.com and Layer3.












